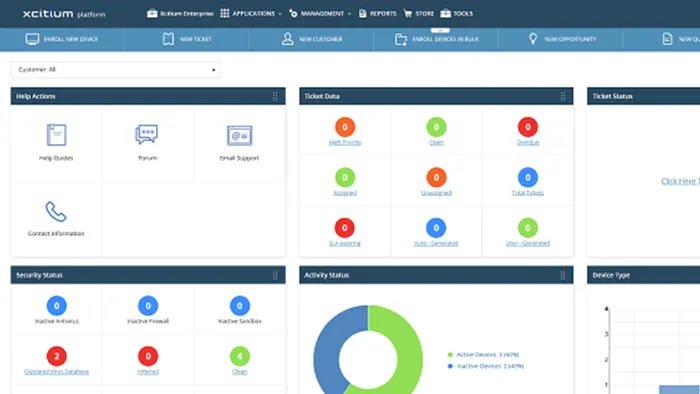
Xcitium Dashboard
Xcitium แดชบอร์ด รวมทุกสิ่งที่จำเป็นไว้ในหน้าเดียว ไม่ว่าจะเป็นการแสดงผลเกี่ยวกับระบบ สถานะการเชื่อมต่อกับอุปกรณ์ต่างๆ ที่ได้ลงทะเบียนไว้ในระบบ ประกอบกับแผนภูมิ แสดงผลการทำงานของอุปกรณ์ต่างๆ ที่สามารถปรับแต่งได้ด้วยตัวเอง รวมทั้งไม่พลาดการแจ้งเตือนสำคัญ พร้อมทั้งสร้างรายงานได้อย่างสะดวก
ADVANCED ENDPOINT PROTECTION
Endpoint Security Benefits
While unknown files are in containment, the files are immediately analyzed in the cloud by Xcitium’s Valkyrie Verdicting Engine and Threat Intelligencewithout interrupting the end user.
Secure your Endpoints from Ransomware, Data Breaches, & Malware
Advanced Endpoint Protection will never trust and will always verify 100% of unknown executables to prevent any damage
ZERO TRUST ARCHITECTURE
Endpoints Finally Protected
CONTAINMENT WITHOUT COMPROMISE
Outsmart Malware And Attack Vectors
Xcitium Excellence In The Industry
Xcitium solutions and services are recognized by leading industry associations, authorities, and analysts.
Our innovative technologies are securing organizations worldwide.

Endpoint Protection
100% in protection against 0-day malware attacks, inclusive of web and email threats.
100% in the detection of widespread and prevalent malware discovered in the last 4 weeks.
Malware Protection
Xcitium Advanced Endpoint Protection can protect against the unknown file and solves the malware problem

Endpoint Protection
4.3/5 Rating for Endpoint Protection Platform
83% Recommend Xcitium
IT and Security Management Platform
2018 Trust Award Best Managed Security Service
2019 Finalist Threat Intel Technology
Endpoint Protection 60x | Awards in Firewall
4.2 /5 Rating for Endpoint Protection Platform
4.3 /5 Rating for Advanced Endpoint Protection
4.5 /5 Rating for Endpoint Detection and Response

Advanced Endpoint Security and Internet Security
Last test: March 2022
Recent result: 100%
2x | 2022 Excellence Award
Total awards granted: 16
Product of the year: 2021, 2020