Endpoints are finally protected
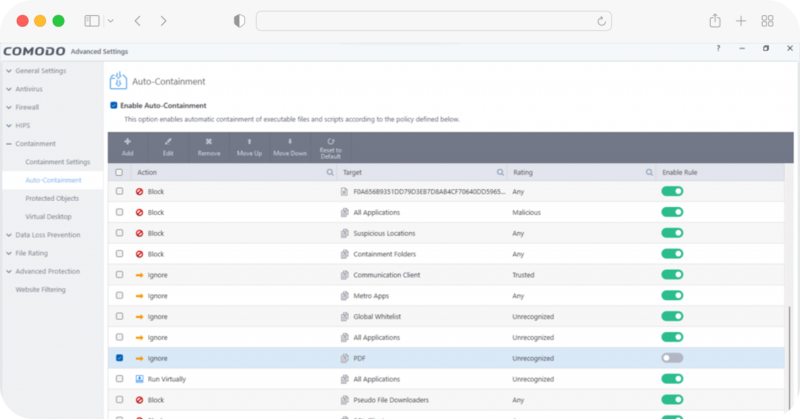

Eliminate Threats That Bypass Detection
Untrusted files and other files that require permission to run processes are automatically separated from the physical space and run in the virtual space or container. AI automatically analyzes the files. and stops the process from being able to access the destination machine and host system resources or user data.
Cloud-native updates via the client
Zero threats are quickly deployed through security. It will not have a significant impact on destination performance. End users enjoy smooth performance. With the ability to extract unknown or unreliable files in the virtual space even when the file is being analyzed.
ZeroDwell Containment
Prevents unknowns instantly through denying write access privileges of any unknowns
NGAV & Award-winning Firewall
Powerful real world antivirus to automatically detect, cleanse and quarantine suspicious files
Fileless Malware Protection
Protection against fileless malware payloads that bypass any traditional antivirus
Virus Scope Behavior Analyzer
Protection against fileless malware payloads that bypass any traditional antivirus
Xcitium Host Firewall
Keep incoming threats out as well steer clear of any suspicious threats going outbound.
Host Intrusion Prevention System
Continuous monitoring of operating system activities to detect intrusions before any trespassing can occur
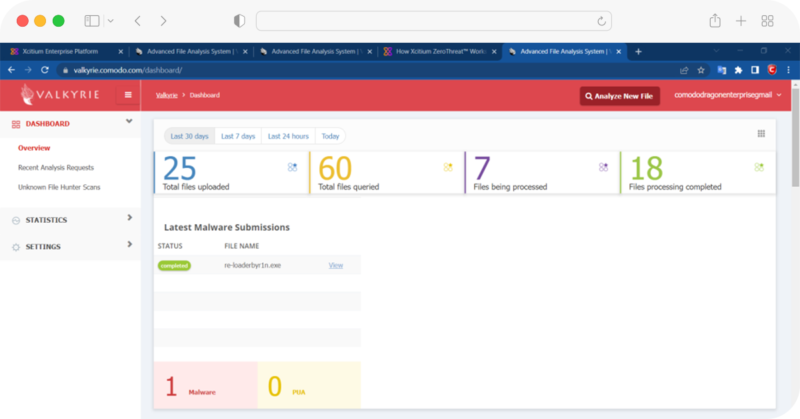
Verdict Cloud Intel Analyzers
Real time static and dynamic scans across the cloud, deep web, and dark web for unknowns against your organization.
Xcitium File Reputation Lookup
Cross reference any file’s threat reputation against one of the world’s largest whitelist and blacklist threat intelligence.
Cloud Based Updates
New malware signatures are consistently delivered through the cloud to ensure both security and optimal user performance.



