What is Ransomeware Cyber Threats What Businesses Should Know?

Let’s get to know Ransomware. Why should businesses be cautious?
Currently, there is frequent news about “Ransomware” that we often come across. But what exactly is it? Let’s explain it in simple terms for better understanding. Ransomware is a type of malware that is not designed to steal data from user devices. Instead, it encrypts or locks files, such as documents, images, and videos, making them inaccessible to users. If these files are encrypted, users cannot open them unless they have the “key” to unlock and recover the data. Users are then required to pay a ransom as stated in the ransom message that appears.

The text “Ransom” will appear after the files have been successfully encrypted. The ransom amount can vary, typically ranging from $150 to $500 (approximately 5,000 to 10 Thai Baht). Payment must be made through a system that is difficult to trace or track, such as electronic transfers, Paysafecard, or Bitcoin. However, it is important to note that making the payment does not guarantee that malicious actors will send the key to unlock the files to the user. This cyber threat can disrupt business operations and lead to significant data loss for organizations.
In what forms does Ransomware Malware disguise itself ?
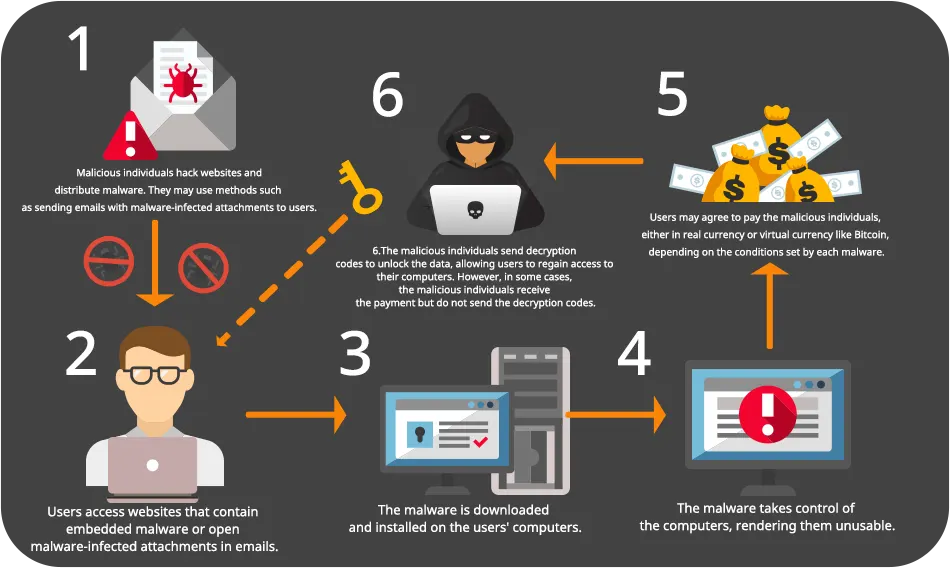
According to the Sonic wall Cyber Threat Report (Mid Year Update 2021), it was found that Ransomware attacked networks up to 307.7 million times, an increase of 151% compared to the same period in 2020. This is the highest recorded number to date. Ransomware distribution can take various forms, such as: [Please provide the remaining content for translation]
ข้อมูลอ้างอิงจาก https://www.scb.co.th
What are some methods to prevent becoming a victim of Ransomware?

Introducing Xcitium, an Anti-Malware program that protects and mitigates attacks from Ransomware.

Xcitium is a Cloud-based Cyber Security technology that ensures the security of devices both within and outside the organization. It operates from any location and on any device, providing on-demand access at all times. With its advanced endpoint protection, Xcitium offers compelling Endpoint Security solutions for businesses, safeguarding data from Ransomware. It guarantees advanced 100% endpoint protection, refusing to trust or execute unfamiliar processed files to prevent potential harm.
The Xcitium program can do the following:
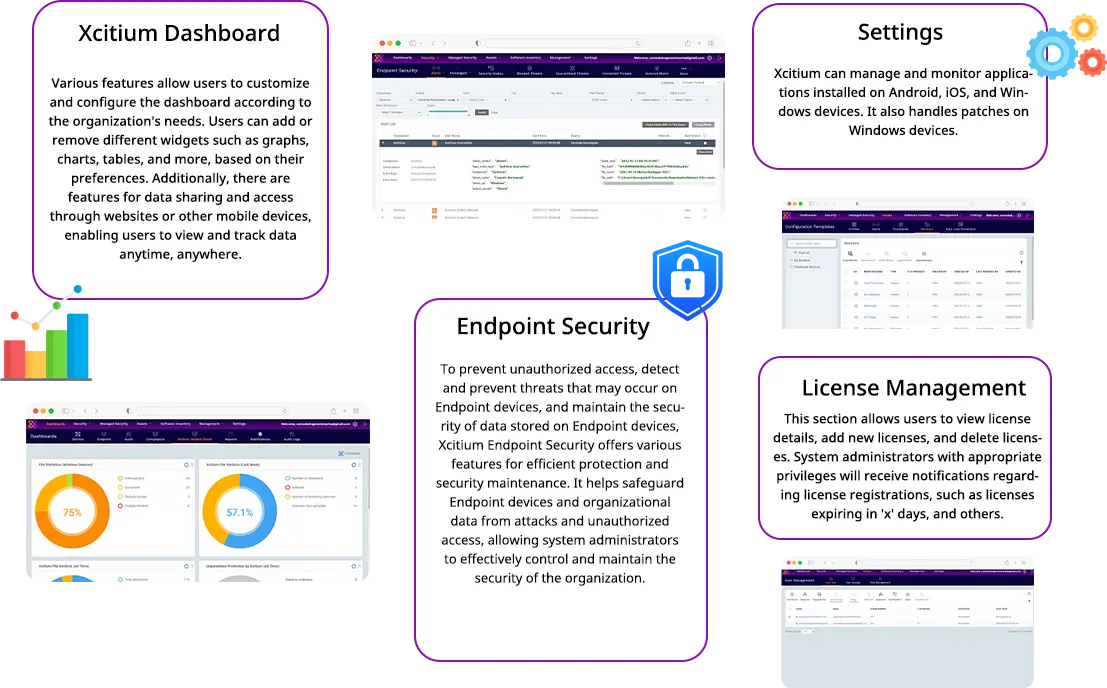
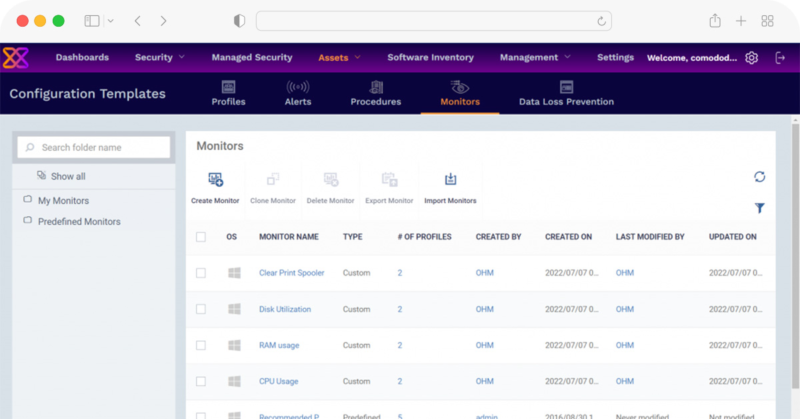
Xcitium Dashboard
Xcitium Dashboard
Various features allow users to customize and configure the dashboard according to the organization’s needs. Users can add or remove different widgets such as graphs, charts, tables, and more, based on their preferences. Additionally, there are features for data sharing and access through websites or other mobile devices, enabling users to view and track data anytime, anywhere.
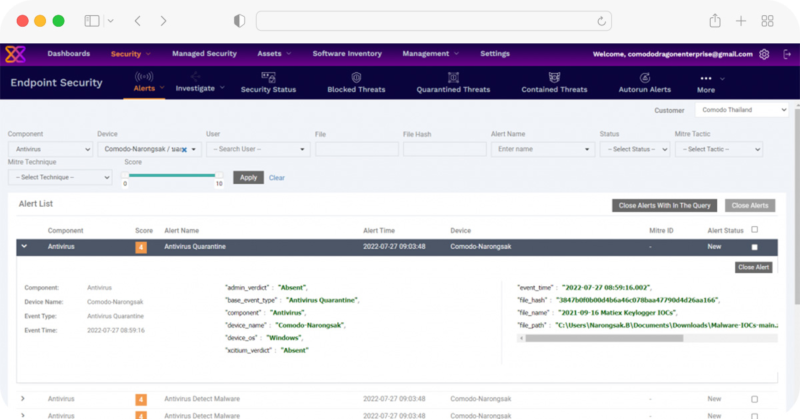
Endpoint Security
Endpoint Security
To prevent unauthorized access, detect and prevent threats that may occur on Endpoint devices, and maintain the security of data stored on Endpoint devices, Xcitium Endpoint Security offers various features for efficient protection and security maintenance. It helps safeguard Endpoint devices and organizational data from attacks and unauthorized access, allowing system administrators to effectively control and maintain the security of the organization.
Xcitium Setting
Settings
Xcitium can manage and monitor applications installed on Android, iOS, and Windows devices. It also handles patches on Windows devices.
License Management
License Management
This section allows users to view license details, add new licenses, and delete licenses. System administrators with appropriate privileges will receive notifications regarding license registrations, such as licenses expiring in ‘x’ days, and others.
For more information, please visit https://www.aquaorange.co.th/xcitium/xcitium-thailand/
Xcitium Advanced Feature Capabilities
ZeroDwell Containment
Prevents unknowns instantly through denying write access privileges of any unknowns
NGAV & Award-winning Firewall
Powerful real world antivirus to automatically detect, cleanse and quarantine suspicious files
Fileless Malware Protection
Protection against fileless malware payloads that bypass any traditional antivirus
Virus Scope Behavior Analyzer
Protection against fileless malware payloads that bypass any traditional antivirus
Xcitium Host Firewall
Keep incoming threats out as well steer clear of any suspicious threats going outbound.
Host Intrusion Prevention System
Continuous monitoring of operating system activities to detect intrusions before any trespassing can occur
Verdict Cloud Intel Analyzers
Real time static and dynamic scans across the cloud, deep web, and dark web for unknowns against your organization.
Xcitium File Reputation Lookup
Cross reference any file’s threat reputation against one of the world’s largest whitelist and blacklist threat intelligence.
Cloud Based Updates
New malware signatures are consistently delivered through the cloud to ensure both security and optimal user performance.
How important of Endpoint Detection and Response (EDR)?
For those interested in installing the Xcitium program, you can use the AquaOrange service [link] to easily perform the installation on both business and personal devices.
For more information, please visit https://www.aquaorange.co.th/xcitium/xcitium-thailand/
ขอบคุณข้อมูลอ้างอิงจาก
เว็บไซต์ www.scb.co.th/th และ เว็บไซต์ www.it.chula.ac.th
- 3 กรกฎาคม 20233,034
ไวรัสคอมพิวเตอร์ (Computer Virus) คือ โปรแกรมที่ถูกสร้างขึ้นมาเพื่อการโจมตีระบบรักษาความปลอดภัยของคอมพิวเตอร์ ก่อกวน โจรกรรม และทำลายข้อมูลภายในคอมพิวเตอร์
- 7 มิถุนายน 20231,302
Ransomware คือ มัลแวร์ (Malware) ประเภทหนึ่ง ที่ไม่ได้ถูกออกแบบมาเพื่อขโมยข้อมูลบนอุปกรณ์ของผู้ใช้งาน แต่จะ ทำการเข้ารหัสหรือล็อกไฟล์




